“Cloud computing” takes hold as 69% of all internet users have either stored data online or used a web-based software application
Some 69% of online Americans use webmail services, store data online, or use software programs such as word processing applications whose functionality is located on the web. In doing so, these users are making use of “cloud computing,” an emerging architecture by which data and applications reside in cyberspace, allowing users to access them through any web-connected device.
Most internet users are unlikely to be aware of the term “cloud computing.” But online Americans who use webmail services such as Hotmail or Gmail are taking advantage of data storage capabilities managed by a network of computers, which in turn permits access to a user’s email through whatever device he has at hand.
Below is a rundown of the share of internet users who have done a select set of online activities that involve storing data online or accessing applications in cyberspace.
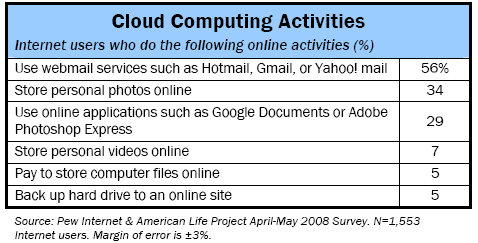
Overall, 69% of online users have done at least one of these six activities, with 40% of internet users having done at least two of them. This list is not meant to include all cloud computing activities. Rather, it is meant to measure a set of common activities associated with cloud computing. Some other online acts associated with cloud computing include storing browser bookmarks online, storing presentations on a website and showing them through a browser, and using social networking sites.
Convenience and flexibility are the watchwords for those who engage in cloud computing activities:
- 51% of internet users who have done a cloud computing activity say a major reason they do this is that it is easy and convenient.
- 41% of cloud users say a major reason they use these applications is that they like being able to access their data from whatever computer they are using.
- 39% cite the ease of sharing information as a major reason they use applications in cyberspace or store data there.
At the same time, users report high levels of concern when presented with scenarios in which companies may put their data to uses of which they may not be aware.
- 90% of cloud application users say they would be very concerned if the company at which their data were stored sold it to another party.
- 80% say they would be very concerned if companies used their photos or other data in marketing campaigns.
- 68% of users of at least one of the six cloud applications say they would be very concerned if companies who provided these services analyzed their information and then displayed ads to them based on their actions.
This data memo is based on a survey of 2,251 adults between April 8, 2008 and May 11, 2008. Some 1,553 respondents in the survey were internet users and the margin of error is plus or minus 3 percentage points for results based on internet users.
Background
The term “cloud computing” has gained currency in the information technology world in the past 18 months as a way to describe the ongoing evolution in how people access and manage digital information.
Years ago, computing was largely centralized. Users accessed information on mainframe computers from terminals that had very little computing power. With the advent of the personal computer in the 1980s, processing power came to the individual’s desktop with basic applications such as spreadsheets and word processing. Although some of these machines, such as those in large organizations, might have been networked through a mainframe, a good bit of data transfer took place on foot, as people carried floppy disks from computer to computer.
As internet adoption became mainstream in the 1990s, the network of networks increased the power of decentralized computing. Personal computers not only stored data locally, but could also download and exchange data found far and wide on the world wide web. The growth in broadband access to the desktop at home and work has been a force multiplier to this model of computing.
Recent evolutions in information technology have led to a more distributed computing environment, while also reviving the utility of centralized storage. The growth in high-speed data lines, the falling cost of storage, the advent of wireless high-speed networks, the proliferation of handheld devices that can access the web – together, these factors mean that users now can store data on a server that likely resides in a remote data center. Users can then access the data from their own computer, someone else’s desktop computer, a laptop that wirelessly connects to the internet, or a handheld device.
Users face new challenges as they try to manage their data that might be stored in a variety of devices. This is where cloud computing enters the picture, a term often used in the same context as grid computing or utility computing. Still, there are distinctions. Whereas utility computing is seen as a business model, such as Amazon.com’s “Amazon Web Service” (AWS) that rents storage space and access to companies, cloud computing refers more broadly to a computing architecture. This architecture links computers in a grid and allows users to buy access to data and software stored on the grid or processing power that is harnessed for specific purposes by the grid of computers.1
Cloud computing is often seen as particularly useful to large corporations. A company may have employees in numerous locations running specialized software to carry out data-intensive tasks. Accessing data and software might be practically impossible without a grid of networked computers. These computing resources are drawn from someplace beyond the user’s location, and the fact that they exist at an ill-defined elsewhere is the source of the image that they come from a cloud.
The Cloud and Online Activities
For everyday users of the internet and computers, cloud computing is any online activity, such as accessing data or using a software program, which can be done from different devices regardless of the on-ramp to the internet. Someone might use the same device but different network access points – think of the laptop user logging on via a WiFi network at a train station or at the office on a wired network. Or it may mean using a terminal at a business center at a hotel or a friend’s computer to check email or view photos. Most ambitiously, as Microsoft’s Ray Ozzie has said, cloud computing would enable “a personal mesh of devices – a means by which all of your devices are brought together, managed through the web as a seamless whole.”2
In this vision, the data or software applications are not stored on the user’s computer, but rather are accessed through the web from any device at any location a person can get web access. This raises issues for users which they may or may not fully appreciate. Trust comes to the fore; if one is to rely on the cloud, one has to trust that data and services will be there when called upon. Control is another issue, closely related to trust. A user trusting the cloud faces loss of control over personal information stored on a disembodied network. Reliability and security thus become important values in making the cloud functional for users.
Using the Cloud: WiFi connectors are enthusiastic and younger users are the most avid adopters.
This data memo takes a snapshot at the prevalence of the use of online services to store personal information or access software. Our May 2008 survey asked about six different online behaviors that would qualify as using cloud computing resources. This is not intended to be a comprehensive portrait of cloud usage, but rather – for a select set of activities – an overview of how many internet users let the network be the steward of data and applications that have typically been on the personal computer.

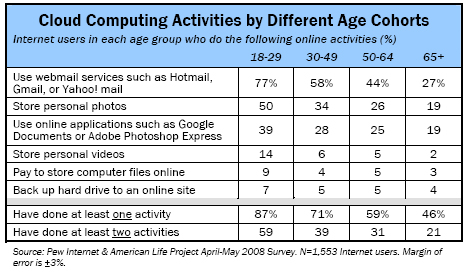
Overall, 69% of internet users have done at least one of the six activities listed above and 40% have done at least two.
Those with mobile computer access “on the go”, that is, those who use a laptop to go online away from home or work using a WiFi connection, are more likely to have done these activities. Among the 34% of online users who have used a WiFi connection on their laptop to go online, 79% have done one of the six activities listed above, and 52% have done at least two.
Although cloud computing may connote the notion of mobile wireless use, the concepts are related only in that wireless networks and devices permit another on-ramp to cyberspace. Wireless access gives users greater incentive to take advantage of cloud computing, but it is not something that, in itself, is a cloud computing activity.
Younger internet users are more inclined than older ones to use services or applications that require personal data be stored online.
The ease and flexibility of cloud applications draw users to them.
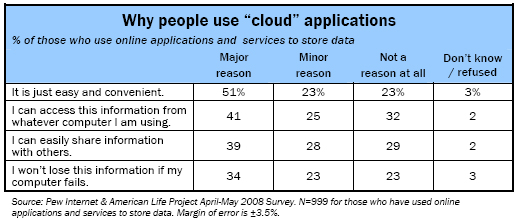
When asked why they use the different services that store personal information on the web, users cite a range of reasons that have mostly to do with ease and flexibility. They like how such services enable them to share data with others and let them easily access their data from any computer.
Roughly half (51%) of those who have done at least one of the listed cloud applications say that ease and convenience are a major reason why they use an application that has them storing personal data on the web. Some 41% say a major reason they use such applications is that they want to access information no matter what computer they are using.
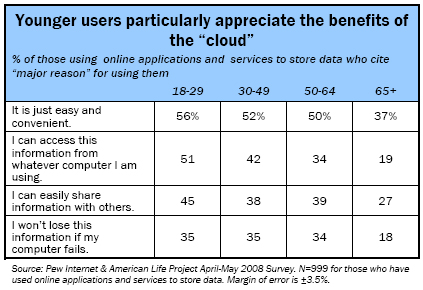
Younger users of cloud applications are more likely to herald the benefits of storing information or accessing software applications online.
Cloud users to providers: let’s keep the data between us.
Against people’s appreciation of the ease and flexibility of cloud applications is concern about control of the information they store on the web. Online Americans who have used at least one of the listed services or applications were further queried about their views on data policies that providers of such services might have in effect. For example, targeted online advertising – the practice by which users’ online behavior is analyzed so that ads relevant to their apparent interests can be served to them – is common in cyberspace. However, as the Federal Trade Commission has noted, “while behavioral advertising provides benefits to consumers in the form of free web content and personalized ads that many consumers value, the practice itself is largely invisible and unknown to consumers.”3
As the figures show, cloud users show high levels of concern when presented with scenarios in which companies might use their data for purposes users may or may not fully understand ahead of time. This suggests user worry over control of the information they store online. For nearly all of the scenarios shown, most users of cloud applications say they would be very concerned if their data were sold, used in marketing campaigns, not deleted as requested, or used for targeted ads.
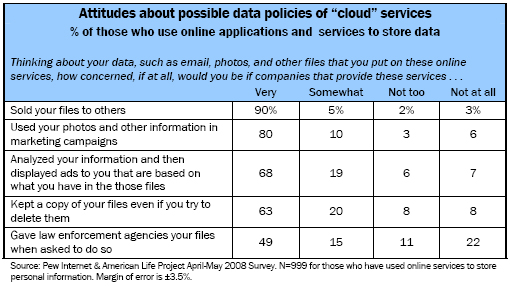
It is worth noting that this survey’s finding that 68% of cloud users are very concerned about targeted ads based on online behavior is not too dissimilar from a March 2008 Harris Interactive/Alan F. Westin survey. That study found that 59% of adults were not comfortable with ads targeted to them based on their online activity; the Harris question noted that these ads help enable free services such as webmail.4 A recent report by TRUSTe, an organization that provides a seal to identify trustworthy online organizations, found that most (71%) online users are aware that third parties may collect information about them for advertising purposes, but that 57% were not comfortable with advertisers using such information to serve ads to them.5
These studies focus on internet users as consumers, but cloud applications extend beyond people’s consumer behavior to activities oriented toward socializing, as well as gathering and sharing information. This information may be as basic as checking news headlines, or more sensitive in nature, such as searches for health or medical information. People’s perspectives on secondary use of personal information stored in the cloud or third-party analysis of data may vary widely across the great range of things people do online. This leaves fruitful avenues for researchers as more people begin to use cloud computing applications. And it suggests there is a wide scope for public education on the details of these emerging applications.
About the Pew Research Center’s Internet & American Life Project
The Pew Research Center’s Internet Project is an initiative of the Pew Research Center, a nonprofit “fact tank” that provides information on the issues, attitudes and trends shaping America and the world. Pew Internet explores the impact of the internet on children, families, communities, the work place, schools, health care and civic/political life. The Project is nonpartisan and takes no position on policy issues. Support for the project is provided by The Pew Charitable Trusts.




